While the first query may not have many action items in the first example due to the limited Domain Admins group membership, let’s click on the pre-built query identified as Find Shortest Path to Domain Admins. This query will take all the information provided and display possible paths that a threat actor could exercise to gain a high level of privilege within an environment.
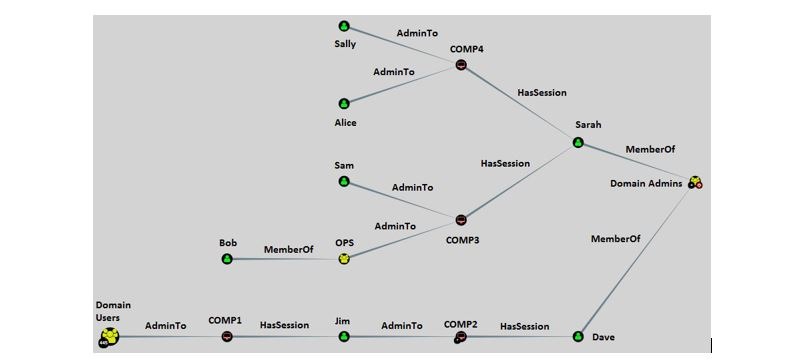
Above we see the same objects where the group of yellow objects are Active Directory security groups, the red monitors are Active Directory computer objects, and the green objects are Active Directory user accounts. However, in this instance, they are laid out in a fashion which has three key pieces of information:
- AdminTo – Indicates that a user or a group of users has local administrative access to a specific computer object. As an example, the group called Domain Users, which has 445 users (indicated by the number in the corner of the object), is a local administrator over the COMP1 computer object.
- HasSession – Indicates that a user has an active session to a specific computer that they have logged on to at some point in the past. Jim has a session to the COMP1 computer.
- MemberOf – Just like in Active Directory lingo, this indicates that a user belongs to an Active Directory Security group. Dave is a MemberOf the Domain Admins security group.
Now that we know what the objects and the lines between objects mean, we can begin deriving actions that we can take to eliminate trust relationships between objects that result in an unintended path for privilege escalation. Let’s start with the example at the bottom of the picture where the Domain Users group with 445 users is a local administrator over the computer of COMP1. Our user Jim has a session to both COMP1 and is a local Administrator COMP2. The issue arises, when our user Dave used his Domain Admin user account to logon to COMP2, which is not a domain controller. It is critical that privileged credentials are treated like an attack surface, which means that the more places a credential is used the higher the likelihood for the credential to be compromised. By instructing users to use a privileged account only where necessary, the overall exposure of the credentials can be limited. Additionally, architecting Active Directory permission structures to avoid the usage of the Domain Admin groups for purposes other than administering a domain should also be in place (role based access security groups should be established for this purpose and should also deny logon rights to Domain Admins). From this scenario, we can derive the following actions items to improve our security posture:
- Remove the Domain Users group from the local Administrators group on computer COMP1. Allowing this group access in the context of the scenario above means that any of the 445 Domain Users can escalate to the Domain Admins security group.
- Perform an entitlement review to ensure that our user Jim needs administrative access to COMP2.
- Enforce technical Group Policy changes so that Domain Admin credentials are denied logon to any system that is not a Domain Controller.
- Initiate an education campaign to remind users that their Domain Admin accounts should not be used on computers that are not a Domain Controller.
For the second example that we’ll look at, let’s assume that the user Bob clicked on a phishing link and a threat actor now has remote access to his computer. If the threat actor is aware of the trust relationships between computer objects within our demo domain, the threat actor could compromise COMP3 with the access already obtained because Bob is a member of the OPS security group, which is a part of the local Administrators group on COMP3. Sarah made the same mistake that our user Dave did in the previous example, and logged onto COMP3 with her Domain Admin account, which is not a Domain Controller. In this instance, our threat actor can obtain Domain Admin permissions over our domain by only pivoting to one additional host, COMP3. From this scenario, we will have a similar set of action items:
- Initiate an education campaign and additional security controls to help inform users of phishing attacks and to help users identify phishing attempts.
- Perform an entitlement review of the OPS Active Directory security group to ensure that only the users that should be a member are a member.
- Perform an entitlement review of the permissions on the COMP3 computer object to ensure that the OPS group needs to have local administrative access.
- Initiate an education campaign to remind users that their Domain Admin accounts should not be used on computers that are not a Domain Controller.
While the environment that we are looking at in this example is fairly simple, organizations that are much larger have many more systems and privileged groups. We should expect to see many more relationships between systems, users, groups, and domain trusts, which may lead to a full domain compromise.






